The battle between Apple and the FBI over the late San Bernadino shooter’s iPhone 5C has the world watching. Should Apple won the battle, the Government would likely find another case as justification to start another case. If the Government won, this would severely impede the trustworthiness of American software. Whichever way this battle goes, as an innocent bystander you will need to know what is the issue and what can you do about it.

Here’s a nutshell of the backstory if you haven’t been following the case. The FBI wants Apple to install a back door to a particular iPhone that the FBI has in possession. This unit is linked to a terrorist case and the FBI has done all the necessary paperwork to gain access to it. To date, Apple has fulfilled most of FBI’s demands by giving them access to the iPhone owners’ data that lived in Apple’s servers. That is, the FBI has the latest copy of the phone in iCloud containing e-mail, messages, call logs and the like. The FBI wasn’t satisfied with this and asked Apple to create a special version of the iPhone software to allow the FBI to unlock the phone by trying out all passcode combinations to forcibly unlock the phone. At this point Apple refuses because such software could also be used by bad people to undermine the security of all iOS devices. Moreover Apple believes if the government is allowed to win this one case, it would legitimize all subsequent requests to dumb-down all American security software and systems.
But frankly as a civilian, what you need to know boils down to these:
- As of iOS 9.2, it has a weak spot that allows the software to be reinstalled without unlocking or erasing the device. However this is normal – more on this later.
- The FBI doesn’t really need Apple’s help to unlock the particular phone in their possession. Theoretically they can do this themselves.
- Use a strong password to protect your data. Strong passwords makes trying out all combinations not humanly feasible.
iOS’ Weak Spot
What FBI wants is a version of iOS that (a) doesn’t automatically erase the iPhone when an incorrect passcode was entered and (b) allows the passcode to be entered electronically. Apple has tacitly admitted that it is possible to engineer the back door and install it.
Please allow me to spell out that last fragment for you: it is possible to change iOS software without unlocking the device. Yes, this is a weak point for iOS devices. But a similar vulnerability also exists on the Mac. On the Mac, it is possible to reprogram the firmware without unlocking the hard drive (or SSD storage).
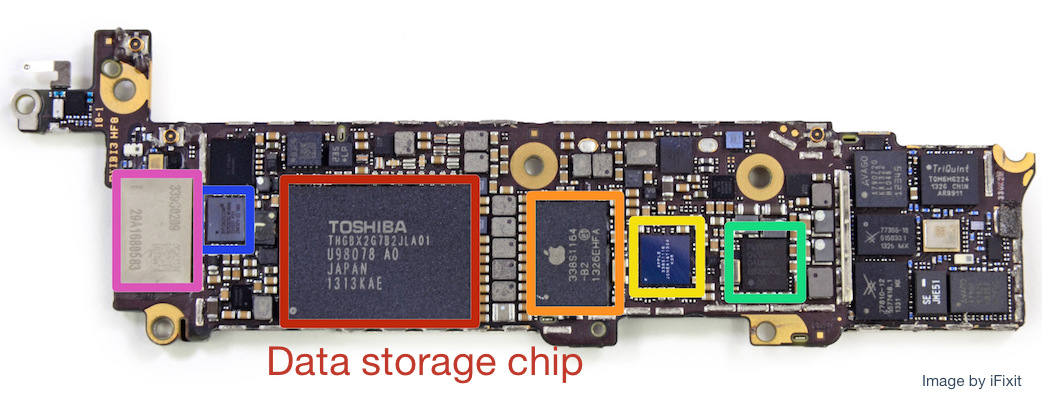
To take the analogy further, it is possible to take out the Mac’s hard drive (or SSD storage) and then use it to try out all passcode combinations in an effort to unlock the drive. In a similar manner it is also possible to do the same thing to an iPhone. As iFixit has shown, the iPhone 5C’s data storage is on a separate chip. The FBI could just de-solder this chip and brute-force unlock it without needing to start iOS. In fact this is one approach that Edward Snowden recommends.
Why the FBI doesn’t Need Apple
As per the examples described above, the FBI doesn’t really need Apple to create the back door they want. What are their real intentions is up to speculation – and I won’t be delving to that direction here.
Moreover it is reasonably possible for the FBI to ask Apple for the iPhone software’s source code. This is without needing to invoke the so-called all writs act. Sure the source code is an intellectual property, but this part can be solved with a relatively simple Non-Disclosure Agreement (NDA). The FBI would need to ensure that the source code won’t leak out to competitors or the general public, but that’s just about all. Besides, a good portion of iOS’ source code is already open for everyone to see.
With iOS’ and firmware source code in hand, there is no technical barrier for the FBI to make the back-door themselves. Yes there may be a need to ask for the firmware’s signing key as well – but this could also be classified as part of the source code.
Recent news revealed that the government admits this themselves. That is, there is a way to brute-force the device without asking Apple for a custom firmware.
Protecting Your Data
As a common user, what should you do? Put simply, you should have a strong password. This would make trying out all combinations (brute force attack) not humanly feasible. It would take about four days to crack a 4-digit PIN, over a year to crack a 6-digit PIN and it would take almost three thousand years to crack a 6-character letter and number combination. These numbers are based on a cracking device at an average rate of 40 seconds per entry. Sure recent iterations of that device could be faster and brute force attacks could be done quicker.
However encryption technologies also grows more complex as processing speeds increase. That is, as processors get faster, the encryption algorithm gets tuned to run slower. In fact in iOS this is calibrated to about 80 milliseconds per entry. Hence a 6-alphanumeric passcode would take about 5.5 years to crack.
In Summary
In short, be sure to have a strong password to your devices. Remember that recent iPhones have finger print recognition to make it less of a hassle to have a longer passcode. Moreover be careful of data that you store “on the cloud” – especially unencrypted data in other people’s servers. No matter how strong your passcode is, it would not matter if you have an open copy of your data residing somewhere else.
That’s all for now. Be safe
